Generating password mutations
Remembering passwords
Almost 30 years ago the internet connected us to all kinds of apps and services. To use these apps & services, we started registering and signing up to accounts. With all these accounts, we then needed to think of a unique password.
Repeating this process of a new, unique password can be tricky though. Our minds can only think of and retain a finite number of passwords, amongst other things. Eventually, we resort to using a single phrase and modifying 1 character each time. A short-term fix for a long term problem.
Let's visualize this with one of the most frequently used passwords I've seen when accessing accounts in non-production apps ... 🥁
Password
Each time a password reset is needed for an account, more often that not the standard is to not re-use the same matching password. To meet security standards and also not have to remember a whole new phrase, we'd probably change 1 character each time a password change is required.
- Password
- PAssword
- P@ssword
- P@ssWord
- P@ssW0rd
And the list goes on. Trying to remember all the previous passwords entered whilst also attempting to try new, unused combinations can be exhausting. Eventually we'll just give up, shut down PC and never use that application again ...
If only there was a program that could do this for me
You - sometime in the past 30 years
The solution
Enter psudohash.
As per the developer's words:
psudohash is a password list generator for orchestrating brute force attacks. It imitates certain password creation patterns commonly used by humans, like substituting a word's letters with symbols or numbers, using char-case variations, adding a common padding before or after the word and more. It is keyword-based and highly customizable.
No more memorizing passwords combos or thinking outside the box. Let psudohash do the thinking for you!
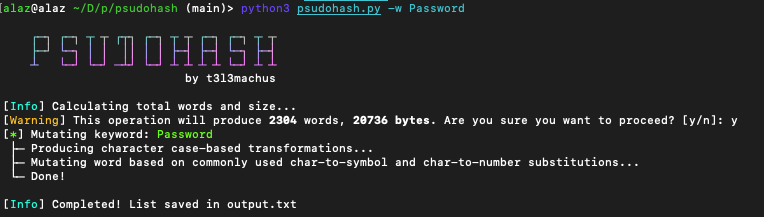
Here's a very basic demo using the phrase Password:
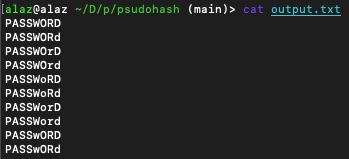
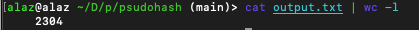
Awesome. Now to retrieve the values generated, let's read output.txt.
And of course, let's confirm that 2304 mutations have been generated using wc to count the lines in ./output.txt.
Brilliant. With just 1 command, we do away with hours of thinking for new combinations. No more brain power needed here!
Multiple mutations
This method of phrase mutations can also be used for penetration testing. For example, let's say you're undergoing a task to break into a web app. You're likely to have limited authentication methods to gain access.
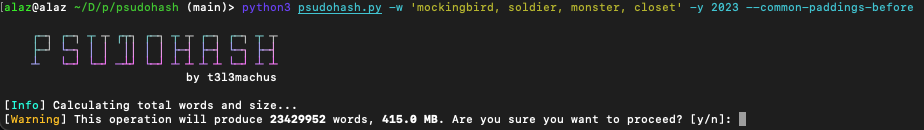
What you can do in this situation is run psudohash, which accepts an array of phrases. What's more, options are available to allow start and ending symbols and year values to the mutations. This combination of arguments opens the door for 1000s of password combinations to be created within seconds.
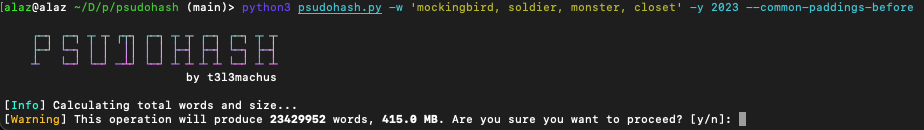
Now 415MB worth of results is a bit much. Let's reduce that array by removing 2 of the 4 phrases.
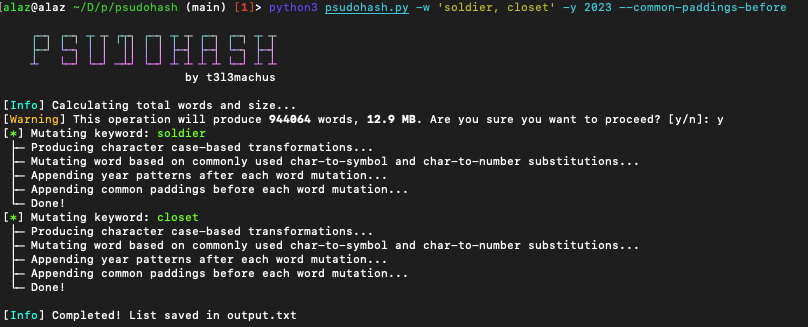
This approach would prove to be infinitely faster, giving you more time to break in and do what you need to do. Let's look at some of those results:
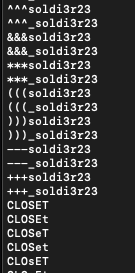
23,429,952 total results produced!Looping through phrases to mutate
Thinking again as a penetration tester, you'd want to combine creative and technical thinking to outwit an application's security. Taking the idea of automation one step further, we can store a list of commonly used passwords, pass that list into psudohash and mutate each item, providing even more combinations to login with.
By default, psudohash stores each result of a mutation into a single output.txt, which replaces the existing file contents. By transferring the run command into a script, I can feed in phrases form a data source, mutate each phrase and save results to an output file.
Script
#!/bin/sh
path_psudohash=./psudohash/psudohash.py
path_dataSource=./data-phrases.txt
countWordsInDataSource=`cat data-phrases.txt | wc -w`
echo reading from datasource: ${path_dataSource}
echo total phrases to mutate: ${countWordsInDataSource}
while IFS= read -r line; do
echo "phrase read from file: <$line>"
echo "~~~~~~~~~~~~~~~~~~~~~~~~~~~~\n"
echo "mutating <$line>"
yes | python3 ${path_psudohash} -w ${line} -y 2023 --common-paddings-before -q -o "mutation-$line.txt"
echo "mutation complete for <$line>"
mutationCount=`cat "mutation-$line.txt" | wc -w`
echo "number of mutations generated for <$line>: $mutationCount"
echo "~~~~~~~~~~~~~~~~~~~~~~~~~~~~\n"
done < ${path_dataSource}
Data source
CLI output
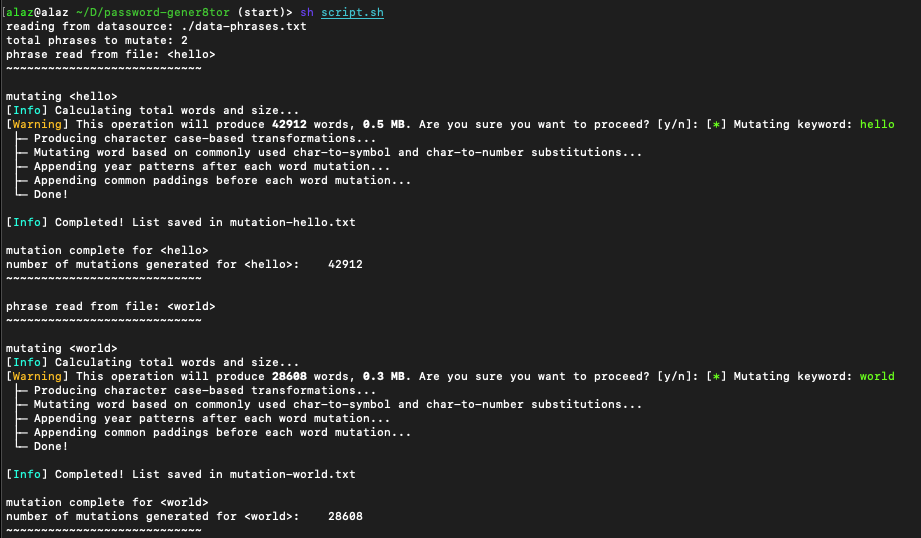
Results
Below are sample values that were generated for the phrases hello and world.
| Hello | World |
|---|---|
| H3lLO | *()WORLd |
| HELLo23 | 123!@#_WORlD |
| +++_HELLO | !!!_WORlD |
| ***_hELlO | @@@_WORlD |
Finale
This has proved to be an awesome tool. The ability to not only jumble up phrases but also include special characters, dates and start/end paddings make generating mutations all that more exciting.
I've stored the looping logic into a repo found here for anyone who wants to toy around with it. I for one, would love nothing more than to push psudohash to its limits and see what unique, creative passwords can be generated.
If you're looking to brute force your way through password-protected systems, psudohash, along with some clever looping logic, will work wonders for you. 🥷
Bonus
Now, being the curious fella I am, I want to try a couple of long phrases and compare results.
Being a dinosaur enthusiast, I instantly recalled my aussie favourite Muttaburrasaurus and passed it into psudohash.
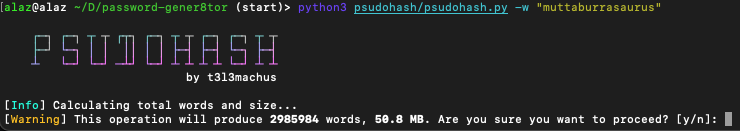
Excellent! This single dinosaur has given a massive file to review. One can only imagine what "Micropachycephalosaurus" would mutate into ...